What does FREAK SSL Vulnerability mean?
FREAK denotes Factoring Attack on RSA-EXPORT Keys.
It is a deficiency in implementing SSL that can allow downgrade attacks and makes easier the violent client’s secure communication decryption. In addition, bad intended people impose end-users to use weaker way of encryption such as 513 bit RSA key or export grade encryption. Consequently, discovering the session keys, the attacker can unimpeded access, steal and use fragile users’ data,
How to know if we are vulnerable?
From the part of users, the most vulnerable are browsers because of bugs which give the opportunity to attackers to force browsers to use a weaker encryption. In addition, software products, mobile apps, are vulnerable as well as browsers.
Not only users are vulnerable, but servers also can be susceptible of accepting RSA export cipher suites and they expose their end-users at dangerous FREAK attack. More than one third of worldwide servers are vulnerable.
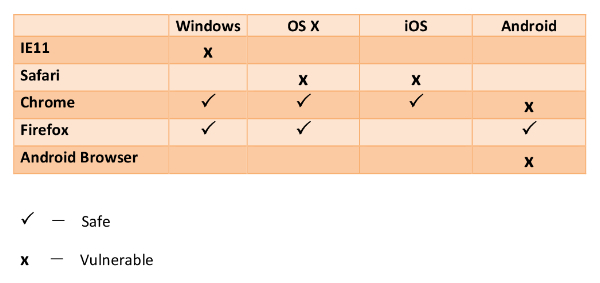
The results of an investigation about browsers’ vulnerability are displayed on the table below.
Steps to improve the situation
Google, Microsoft and Mozilla have made critical updates and patches to their browsers to reduce the impact of the Freak SSL vulnerability.
Moreover, users can check the vulnerability of their browsers on freakattack.com. Eather the result is affirmative or not, a message will be displayed with this confirmation.
How is this happening?
To make a successful FREAK attack possible, not only the browser, but also the server has to apply the export grade encryption at the same time.
Recommendations to prevent the FREAK attack?
- CyberSSL.com recommends do not follow untrusted links or visit untrusted web-sites;
- In addition, end-users shall not access hypertext links contained in web-messages from unknown or untrusted origin;
- Users shall install the newest browsers’ version and update it frequently;
- It is suitable for servers to disable the support for RSA and insecure cipher suites;
- Make testing in time as well as update the vulnerable systems;
- Developers as well as sysadmins shall apply updated TLS libraries as well as ensure that their developed software does not offer export cipher suites.



