- Home
- Security Tools
- SSL checker
Index
- List of tools
SSL tools
- SSL website checker
Free SSL Check: Most advanced SSL analysis
Welcome to our Free SSL Checker tool. Ensure your website's security and protect your visitors' data with our comprehensive SSL certificate analysis.
Certificate Validity
Security Protocols
Vulnerability Scan
DNS Configuration
Our SSL Labs Tool - Recent Scans
Our SSL tool performs comprehensive checks to ensure your site’s SSL certificates are secure and up-to-date. Below are the recent scans and their grades.
Recently Seen
| Website | SSL Score |
|---|---|
| mail.variel.cz | B 80/100✗ |
| lbs.tickerdata.in | F 15/100✗ |
| ovlink.sbs | C 68/100✗ |
| ananthis.free.nf | F 15/100✗ |
| idealagent.com | B 86/100✓ |
| omega-accounting.com | C 68/100✗ |
| charterup.com | C 74/100✗ |
| olsodarugeman.id | B 86/100✓ |
| matsudo-h.com | C 68/100✗ |
| extend.app | A 90/100✓ |
Recent Best
| Website | SSL Score |
|---|---|
| extend.ai | A+ 98/100✓ |
| chat.dimamoska.ru | A+ 98/100✓ |
| chamsocial.com | A+ 98/100✓ |
| mail.tgcab.bank.in | A+ 98/100✓ |
| granmoto.ru | A+ 98/100✓ |
| hopdongcuatoi-uat.manulife.com.vn | A+ 98/100✓ |
| app.nais.pl | A+ 98/100✓ |
| uk4.vpn.cbpg.com | A+ 98/100✓ |
| quantotc.com | A+ 98/100✓ |
| vrb.pmfbl.org | A+ 98/100✓ |
Risk Rating for Website the SSL certificate checker
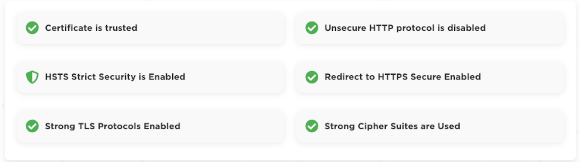
Risk rating for SSL certificates can be influenced by several factors. Here are some key elements that you might consider:
Certificate Authority (CA) Trustworthiness
Certificates issued by well-known, reputable Certificate Authorities are generally considered lower risk. Trusted CAs follow stringent security practices and undergo regular audits to ensure their certification processes are secure and reliable.
Certificate Validity Period
Shorter validity periods are generally safer because they reduce the window for potential compromise. Certificates with shorter lifespans encourage more frequent renewals, which helps in maintaining up-to-date security practices. Conversely, long validity periods might indicate a higher risk, especially if the certificate is not managed properly and regularly monitored for security issues.
Encryption Strength
The strength of the encryption used in the SSL certificate is a crucial factor. For example, 2048-bit RSA encryption is considered secure, but 4096-bit RSA offers even greater security. Using modern encryption algorithms (such as those in the TLS 1.2 or 1.3 protocols) is preferable to older, deprecated algorithms that might be vulnerable to attacks.
Protocol Support
Support for modern protocols like TLS 1.2 and TLS 1.3 indicates a lower risk, as these protocols offer improved security features and are less susceptible to known vulnerabilities. On the other hand, supporting older, less secure protocols such as SSL 2.0, SSL 3.0, and TLS 1.0 can increase the risk of exposure to security flaws.
Vulnerability Status
It is important to check if the site has any known vulnerabilities, such as Heartbleed, POODLE, or BEAST. Using outdated or vulnerable implementations of SSL/TLS can expose the site to potential attacks. Regularly updating and patching the SSL/TLS software helps mitigate these risks.
Certificate Transparency
Certificate Transparency (CT) logs help detect mis-issuance of certificates by providing a publicly auditable record of certificates issued by Certificate Authorities. Ensuring that the certificate is logged in CT logs enhances trust and helps in quickly identifying any unauthorized or fraudulent certificates.
Revocation Status
Properly supporting and regularly checking for revocation status via OCSP (Online Certificate Status Protocol) or CRL (Certificate Revocation List) is crucial. If a certificate is compromised, it needs to be revoked promptly to prevent misuse. Regular revocation checks ensure that users are not exposed to compromised certificates.
Key Usage and Extensions
Proper use of key usage and extensions ensures that certificates are used only for their intended purposes. For example, a certificate intended for server authentication should not be used for code signing. Correctly configured key usage and extensions help in maintaining the integrity and security of the SSL/TLS environment.
Certificate Chain
The validity and security of the full certificate chain, including intermediate and root certificates, are essential. Each certificate in the chain must be valid and secure. A weak link in the chain can compromise the entire SSL/TLS setup. Ensuring that all certificates in the chain are from trusted sources and are properly configured helps in maintaining a secure connection.
Domain Validation Level
Extended Validation (EV) certificates are generally considered lower risk compared to Domain Validation (DV) certificates because EV certificates undergo more rigorous verification processes. EV certificates provide higher assurance about the identity of the certificate holder, which helps in building user trust.
HSTS (HTTP Strict Transport Security)
HTTP Strict Transport Security (HSTS) is a security feature that enforces HTTPS connections. When a site uses HSTS, it instructs browsers to only interact with it over HTTPS, thereby preventing downgrade attacks and cookie hijacking. Implementing HSTS helps ensure that all communications between the user and the site are encrypted and secure, which reduces the risk of man-in-the-middle attacks.
SSL Check Risk and Score Report
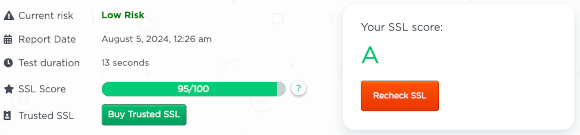
When evaluating the security of your website, an SSL check is crucial for both user trust and SEO performance. Here's a breakdown of what an SSL risk assessment report typically includes:
Current Risk Level
Low Risk: Indicates that your SSL configuration is secure with minimal vulnerabilities.
Recommendations
- Trusted SSL: If your score is lower than desired, consider purchasing a trusted SSL certificate.
- Recheck SSL: Regularly recheck your SSL configuration to maintain security and performance.
Importance for SEO
Using a secure SSL certificate can positively impact your SEO rankings because:
- Google Prefers HTTPS: Websites with HTTPS are more likely to rank higher. Google prioritizes websites with HTTPS, enhancing your search visibility
- User Trust and Confidence: Secure sites foster trust, leading to higher engagement and reduced bounce rates.
- Data Protection: SSL encrypts sensitive information, safeguarding both your site and users.
Benefits of a High SSL Score
- Increased Traffic: Secure websites attract more visitors, improving overall traffic.
- Compliance and Security: Meet regulatory requirements and protect user data effectively.
- Enhanced User Experience: Fast, secure sites lead to better user interactions and satisfaction.
By focusing on SSL checks, you're not only securing your website but also optimizing it for better search engine performance and user engagement. Regular assessments help maintain a secure, trustworthy, and high-ranking website.
SSL Check Vulnerabilities report

An SSL check vulnerabilities report is essential for identifying and addressing potential security risks on your website. Here's what you need to know:
Importance of SSL Vulnerability Checks
- Identify Weaknesses: Detects potential vulnerabilities in your SSL configuration that could be exploited.
- Enhance Security: Helps you strengthen your website's defenses against cyber threats.
Key Components of the Report
- Vulnerability Detection: Lists specific SSL vulnerabilities, such as weak encryption or outdated protocols.
- Severity Levels: Categorizes vulnerabilities by risk level (low, medium, high) to prioritize fixes.
Benefits for Your Website
- User Trust: A secure site builds confidence among visitors, encouraging engagement and reducing bounce rates.
- Compliance: Ensures your website meets security standards and regulations.
- SEO Advantage: Secure websites are favored by search engines, improving your site's ranking potential.
Recommended Actions
- Regular Monitoring: Continuously check for new vulnerabilities to maintain a high level of security.
- Implement Fixes: Address identified vulnerabilities promptly to protect user data and site integrity.
- Upgrade SSL Certificates: Use trusted SSL certificates to ensure strong encryption and security.
Conducting an SSL vulnerabilities report empowers you to proactively manage security risks, safeguarding your website and enhancing its SEO performance. Regular assessments are crucial for maintaining a secure and trustworthy online presence.



